Mythology
artemis-sensei ♦ May 13, 2016 ♦ Leave a comment
Hi, it’s me again.
Did you ever wonder how intriguing and skeptical the Gods and Goddesses in every mythology (Greek, Roman or Norse) are in their stories?
I was first introduced to them when I was in 5th grade in elementary school. I always came to school at least an hour early so I always tend to visit the library. I have read various myths and what really caught and what i think is really cool among them is Artemis.
Well, what made me choose her over the other titans is that even the depiction of their Gods is really similar to us humans, I really love the independence and fierce nature of Artemis. I think I really like her attitude and personality since we are so much alike. Though she has so many sad stories and that involves his twin brother Apollo.
Just look at this (I just don’t know how accurate this one is) :
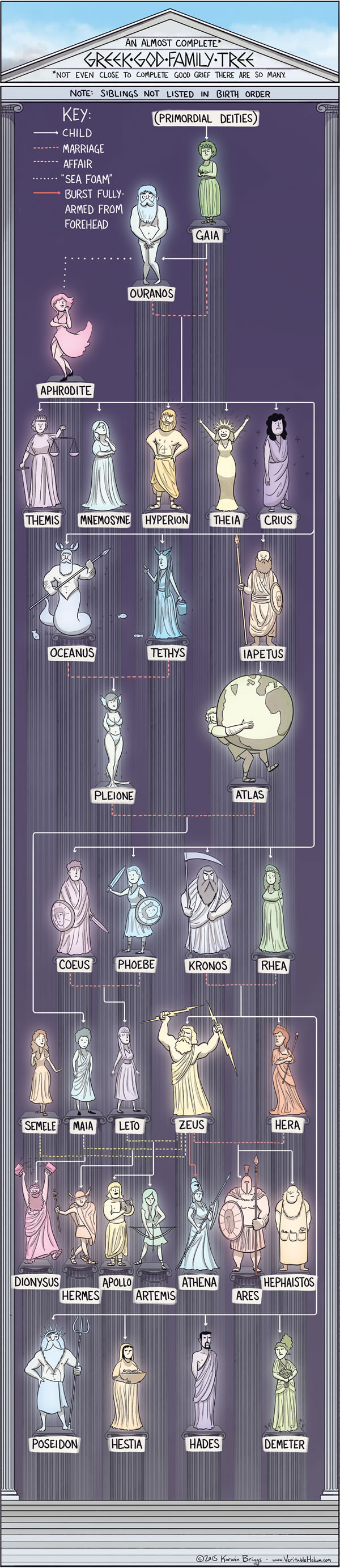
or this one:
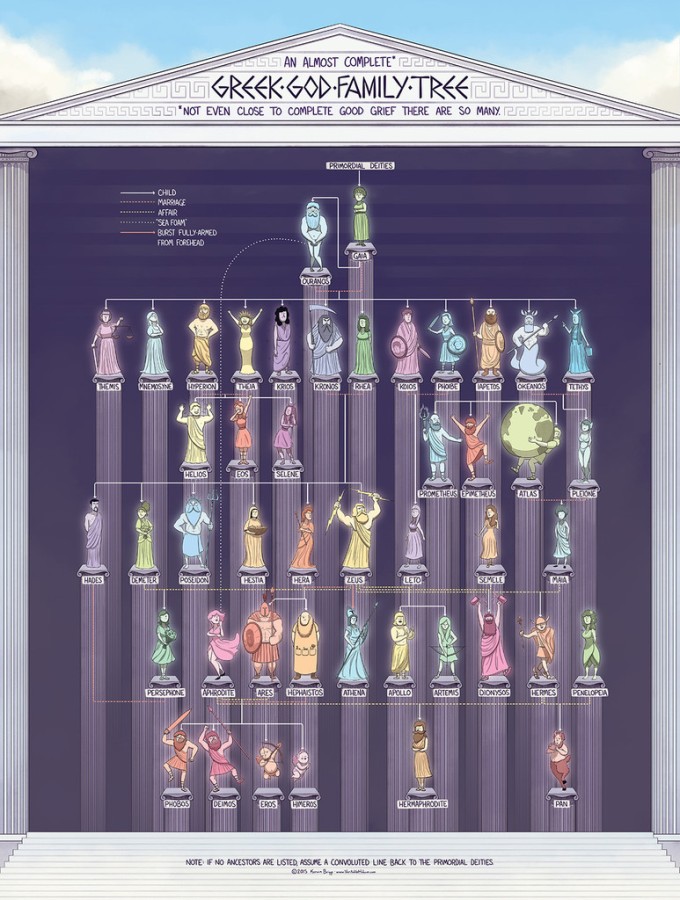
Zeus married his sister and he keeps on impregnating other women. Among others, he got his titan and demigod children by committing adultery. Ain’t that really similar to humans?
Share your own thoughts below:
PRIVACY, SECURITY AND ETHICS AND THE FUTURE OF INFORMATION AGE
artemis-sensei ♦ October 6, 2015 ♦ Leave a comment
Information privacy refers to the right of individuals and companies to deny or restrict the collections and use of information about them.
The information in these electronic profiles includes personal details such as your age, address, telephone number, spending habits, marital status, number of dependents, ages of dependents, and so on.
Spam is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once. Spam is internet junk mail.
Phishing is a scam in which a perpetrator sends an official looking e-mail message that attempts to obtain your personal and personal information.
Pharming is a scam, similar to phishing, where a perpetrator attempts to obtain your personal and financial information, except they do via spoofing.
Clickjacking is yet another similar scam. With clickjacking, an object that can be clicked on a website, such as a button, image, or link, contains a malicious program.
A computer security risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability.
Any illegal act involving a computer generally is referred to as computer crime. The term cybercrime refers to online or internet-based illegal acts. Software used by cybercriminals sometimes is called crimeware.
Perpetrators of cybercrime and other intrusions fall into seven basic categories: hacker, cracker, script kiddie, corporate spy, unethical employee, cyberextortionist and cyberterrorist.
- The term hacker, although originally a complimentary word for a computer enthusiast, now has a derogatory meaning and refers to someone who accesses a computer or network illegally. Some hackers claim the intent of security breaches is to improve security.
- Hackers (or external attackers) try to compromise computers and sensitive information for ill-gotten gains — usually from the outside — as unauthorized users. Hackers go for almost any system they think they can compromise. Some prefer prestigious, well-protected systems, but hacking into anyone’s system increases an attacker’s status in hacker circles.
- Malicious users (or internal attackers) try to compromise computers and sensitive information from the inside as authorized and “trusted” users. Malicious users go for systems they believe they can compromise for ill-gotten gains or revenge.
- Ethical hackers (or good guys) hack systems to discover vulnerabilities to protect against unauthorized access, abuse, and misuse. Information security “researchers” typically fall into this category.
- A cracker also is someone who accesses a computer or network illegally but has the intent of destroying data, stealing information or other malicious action. Both hackers and crackers have advanced computer and network skills.
- Crackers break into, or crack, systems with malicious intent. The personal gain they seek could be fame, profit, and even revenge. They modify, delete, and steal critical information, often making other people miserable.
- A script kiddie has the same intent as a cracker but does not have the technical skills and knowledge. Script kiddies often use prewritten hacking and cracking programs to break into computers.
- Some corporate spies have excellent computer and networking skills and are hired into a specific computer and steal its propriety data and information, or to help identify security risks in their own organization. Unscrupulous companies hire corporate spies, a practice known as corporate espionage, to gain competitive advantage.
- Unethical employees may break into their employers’ computers for a variety of reasons. Some simply want to exploit a security weakness. Some simply want to exploit a security weakness. Others seek financial gains from selling confidential information. Disgruntled employees may want revenge.
- A cyberextortionist is someone who uses e-mail as a vehicle for extortion. These perpetrators send an organization a threatening e-mail message indicating they will expose confidential information, exploit a security flaw, or launch an attack that will compromise the organization’s network – if they are not paid a sum of money.
- A cyberterrorist is someone who uses the internet or network to destroy or damage computers for political reasons. The cyberterrorist might target the nation’s air traffic control system, electricity-generating companies, or a telecommunications infrastructure. The term, cyberwarfare, describes an attack whose goal ranges from disabling a government’s computer network to crippling a country. Cyberterrorism and cyberwarfare usually require a team of highly skilled individuals, millions of dollars and several years of planning.
Internet and network attacks
- A computer virus is a potential damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without the user’s knowledge or permission.
- A worm is a program that copies itself repeatedly, using up resources and possibly shutting down the computer or network.
- A Trojan horse is a program that hides within or looks like legitimate program.
- A rootkit is a program that hides in a computer and allows someone from a remote location to take control of the computer.
- Malware delivers its payload on a computer in a variety of ways: when a user
- opens an infected file
- runs an infected program
- boots the computer with infected removable media inserted in a drive or plugged in a port
- connects an unprotected computer to a network, or
- when a certain condition or event occurs, such as the computer’s clock changing to a specific date. Today, a common way computers become infected with viruses and other malware is through users opening infected e-mail attachments
- A denial of service attack, or DoS attack, is an assault whose purpose is to disrupt computer access to an Internet service such as the Web or e-mail. Perpetrators carry out a DoS attack in a variety of ways.
- A back door is a program or set of instructions in a program that allow users to bypass security controls when accessing a program, computer, or network.
- Spoofing is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network. Several types of spoofing schemes exist. One type, called e-mail spoofing, occurs when the sender’s address or other components of the e-mail header are altered so that it appears the e-mail originated from a different sender.
- A firewall is hardware and/or software that protects a network’s resources from intrusion by users on another network such as the Internet. A personal firewall is a utility program that detects and protects a personal computer and its data from unauthorized intrusions.
Identifying and Authenticating Users
- An access control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer. In addition, the computer should maintain an audit trail that records in a file both successful and unsuccessful access attempts. An unsuccessful access attempt could result from a user mistyping his or her password, or it could result from a hacker trying thousands of passwords.
- Many systems implement access controls using a two-phase process called identification and authentication. Identification verifies that an individual is a valid user. Authentication verifies that the individual is the person he or she claims to be. Three methods of identification and authentication include user names and passwords, possessed objects, and biometric devices.
- Some Web sites use a CAPTCHA to further protect a user’s password. A CAPTCHA, which stands for Completely Automated Public Turing test to tell Computers and Humans Apart, is a program developed at Carnegie Mellon University to verify that user input is not computer generated. A CAPTCHA displays a series of distorted characters and requires the user enter the characters correctly to continue using the Web site.
Possessed Objects
- A possessed object is any item that you must carry to gain access to a computer or computer facility. Examples of possessed objects are badges, cards, smart cards, and keys. Example is an automated teller machine (ATM) that allows you to access your bank account using a personal identification number (PIN).
- A biometric device authenticates a person’s identity by translating a personal characteristic, such as a fingerprint, into a digital code that is compared with a digital code stored in the computer verifying a physical or behavioral characteristic.
WORKING ETHICALLY
- The word ethical in this context means working with high professional morals and principles. Whether you’re performing ethical hacking tests against your own systems or for someone who has hired you, everything you do as an ethical hacker must be aboveboard and must support the company’s goals. No hidden agendas allowed! This also includes reporting all your findings regardless of whether or not it will create politic backlash.
- Trustworthiness is the ultimate tenet. The misuse of information is absolutely forbidden.
THE FUTURE OF INFORMATION AGE
- Virtual communication & remote work environments
- Smaller & more portable devices
- Enhanced device power and internet speed
- Affordable & cost-efficient devices

Recent Comments